Table of Contents
Types of malware: Relevance
- GS 3: Awareness in the fields of IT, Space, Computers, robotics, Nano-technology, bio-technology and issues relating to intellectual property rights.
What is a malware?
- Malware, or malicious software, is a program designed to gain access to computer systems, normally to harm or exploit any programmable device or network.
- Systems or devices infected with malware will show symptoms such as running slower, sending emails without user action, randomly rebooting, or starting unknown processes.
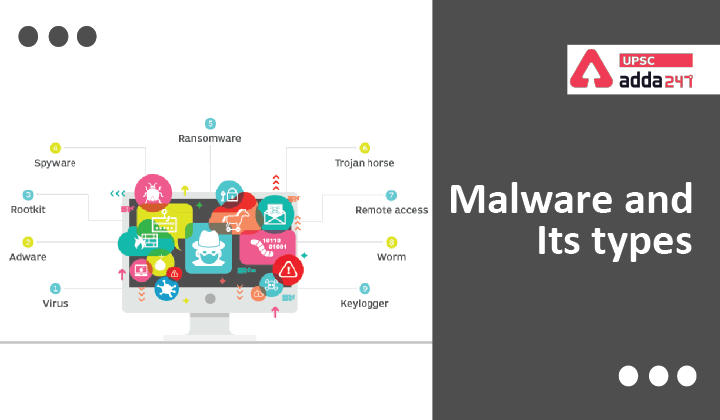
Types of malware
- A malware can come in many forms; however, the most common types are discussed below:
Virus
- Virus is the most commonly known malware type that is capable of infecting other files and spreading to other computers.
- A virus is capable of infecting other files and spreading to other computers. The virus spreads when an infected file is passed from system to system.
- In this sense, they do not spread on their own and require an unsuspecting user to execute them for the initiation of the malicious behaviour.
Worms
- A worm is very much like a virus but it can self-replicate without a host program and spreads without any human interaction.
- Worms usually slow down networks. A virus needs a host program to run but worms can run by themselves.
- After a worm affects a host, it is able to spread very quickly over the network.
Spyware
- It is a type of malware whose purpose is to steal private information from a computer system for a third party. Spyware collects information and sends it to the hacker without the user’s knowledge.
- Attackers usually spy on information such as passwords or pins (usually through key loggers), credit card information, intellectual property or other personal information.
Trojan horse
- Trojan horses (or Trojan), as the name suggests, disguise themselves as desirable code or normal file or program to trick users into downloading and installing them.
- A Trojan horse varies from a virus as a trojan horse binds itself to non-executable files, such as image files, audio files.
- One popular attack type is displaying a pop up that claims the victim’s computer is infected, so that the user can be tricked into installing the malware that masquerade as an antivirus program.
- Trojans are one of the most common malware and are it is hard to defend against them. This is due to the fact that they spread by tricking users, which eliminates many traditional or technical control measures to prevent them.
Ransomware or Crypto-malware
- It is one of the most prevalent types of malware.
- A ransomware is a malware that uses encryption to disable a victim’s access to its own data and demands a ransom, usually in a cryptocurrency in return to decrypt the encrypted data.
Rootkit
- It is a type of malware that gives attackers remote control of a victim’s computer with full administrative privileges.
- In most of the cases, they spread through malicious downloads, phishing or malicious attachments.
Logic bombs
- A logic bomb is a malicious program that uses a trigger to activate the malicious code. The logic bomb remains non-functioning until that trigger event happens.
- Once triggered, it implements a malicious code that causes harm to our computer.
- Cybersecurity specialists have discovered logic bombs that attack and destroy the hardware components in a workstation or server. The logic bomb overdrives these devices until they overheat or fail.
Ways to prevent malware attacks
Though it is not completely possible to eliminate the malware attacks, following can be the proposed solutions to mitigate the malware attacks:
- Develop updated security policies
- Implement security awareness training programmes
- Use of App-Based Multi-Factor Authentication
- Install Anti-Malware & Spam Filters.
- Perform routine vulnerability assessments
Also Read:




 TSPSC Group 1 Question Paper 2024, Downl...
TSPSC Group 1 Question Paper 2024, Downl...
 TSPSC Group 1 Answer key 2024 Out, Downl...
TSPSC Group 1 Answer key 2024 Out, Downl...
 UPSC Prelims 2024 Question Paper, Downlo...
UPSC Prelims 2024 Question Paper, Downlo...




